Introducing Privacy Pass authentication for Kagi Search

Today we are announcing a new privacy feature coming to Kagi Search. Privacy Pass is an authentication protocol first introduced by Davidson et al., in [1], and recently standardized by the IETF as RFCs [2—4]. Our starting point was the excellent Rust implementation of the Privacy Pass protocols by Raphael Robert. At the same time, we are announcing the immediate availability of Kagi’s Tor onion service.
In general terms, Privacy Pass allows “Clients” (generally users) to authenticate to “Servers” (like Kagi) in such a way that while the Server can verify that the connecting Client has the right to access its services, it cannot determine which of its rightful Clients is actually connecting. This is particularly useful in the context of a privacy-respecting paid search engine, where the Server wants to ensure that the Client can access the services, and the Client seeks strong guarantees that, for example, the searches are not associated with them.
As a privacy-respecting search engine, Kagi’s business model is such that we have no incentive to track what an individual user is searching for. We are in the business of selling a search product, not selling user data or attention.
Now, Privacy Pass adds another layer of trust: we can verify that you have the right to search without knowing who you are or what you’re searching for. It’s one thing to promise we won’t track you; it’s another to make it technically impossible. We jumped on the opportunity to implement Privacy Pass as soon as the IETF made it an official standard.
This matters, because for many users, privacy isn’t just about incentives and privacy policies; it’s about proof. When we cannot track you even if we wanted to, that’s genuine privacy.
Initially, we will be offering Privacy Pass to all our plans with unlimited searches: Professional, Ultimate, Family, and Team plans. Privacy Pass will not be available to Trial and Starter plans due to technical limitations at this moment (see below for more info).
To get started with Kagi Privacy Pass right away:
- Download the newest version of Kagi’s Orion Browser (for macOS/iOS/iPadOS) with Kagi Privacy Pass natively integrated. You will need at least 0.99.131 for macOS and 1.3.17 for iOS/iPadOS (they are expected to be rolling out globally today).
OR
- Download the newest version of Kagi for Android app with Kagi Privacy Pass natively integrated. You will need to use at least version 0.29 (this is expected to roll out globally today).
OR
- Download the extension for Firefox or Chrome
- If you are already using the Kagi Search extension, you will want to update it to the latest version (0.7.6 on Firefox, 1.2.2.5 on Chrome) to avoid compatibility issues, or simply disable it.
- Safari is not yet supported due to technical limitations, see the F.A.Q. below.
In addition our implementation of Privacy Pass is open sourced and you can find it here.
When using Kagi Privacy Pass mode, you’ll be truly anonymous - which means your account settings won’t be available since we can’t identify which user you are.
But don’t worry - we’ve made it flexible. You can easily toggle Privacy Pass on or off based on your needs. Think of it as two modes: full features with normal privacy, or maximum privacy with core features. You choose what makes sense for you based on your context and needs.
An overview of Privacy Pass
Privacy Pass uses cryptography to allow a client to authenticate to a server by performing a protocol with two phases: token generation and token redemption.
Token generation
In the initial “token generation” phase, the client interacts with the server to generate some authentication “tokens.”
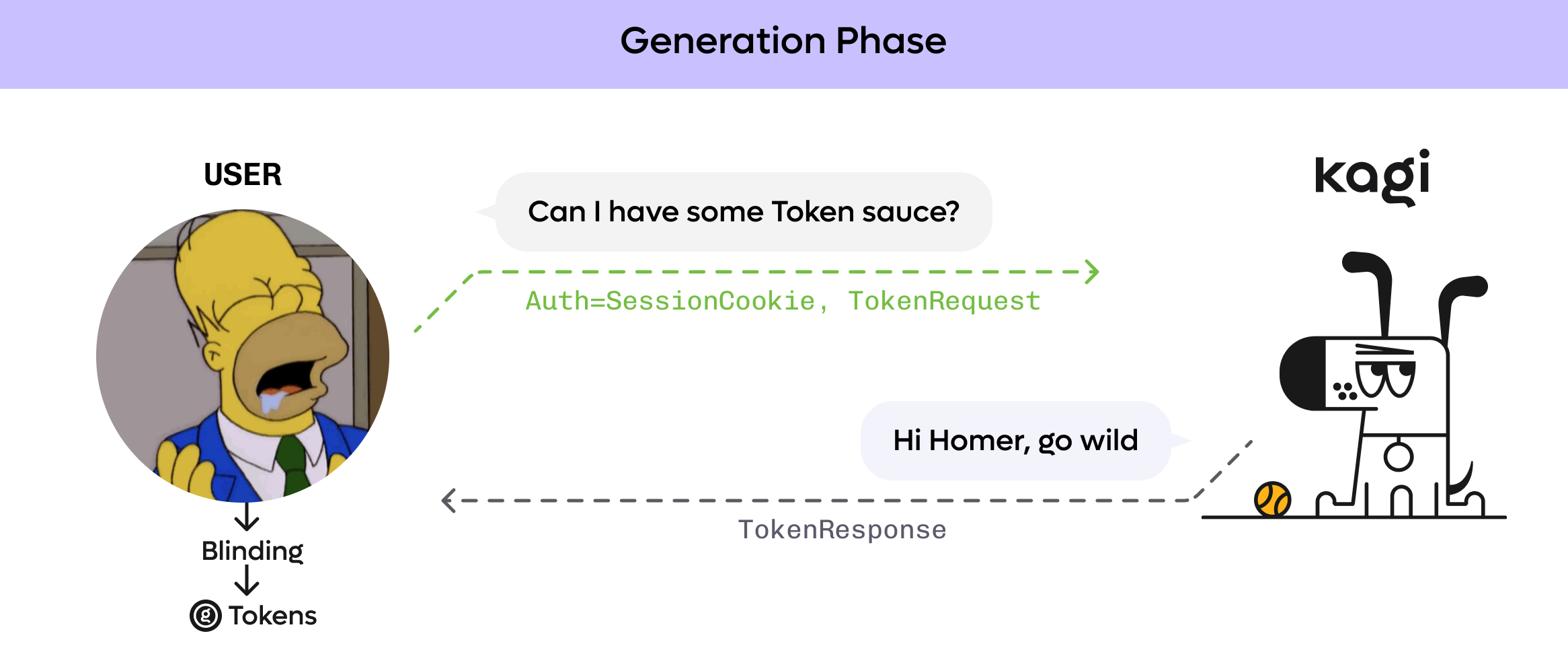
For the server to willingly participate in this protocol, the client must prove their “right” to generate tokens.
In the case of Kagi’s users, this can be done by presenting their Kagi session cookie to the server.
The tokens eventually generated by the client at the end of this phase are indistinguishable from a randomly generated token from the server’s point of view. They cannot be traced back to the user who generated them, or to other tokens generated by the same user at the same or a different time.
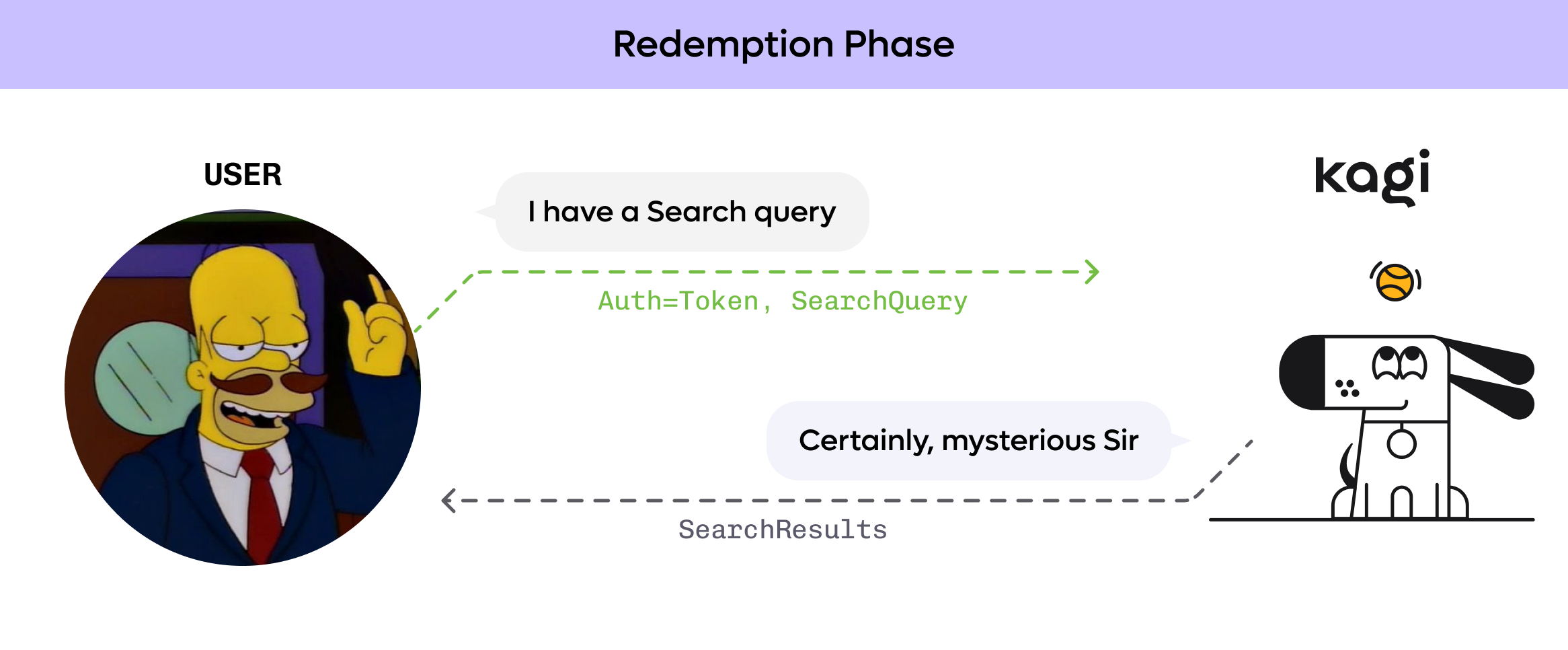
Token redemption
After token generation is performed, a client can initiate a “token redemption” phase.
During this phase, the client actually accesses the services provided by the server, proving the client’s right to access the services by presenting one of the previously generated tokens.
Since the previously generated tokens are unknown and unpredictable to the server, the latter can only tell that the client has successfully completed token generation at some point.
Technically, we say that the techniques used by Privacy Pass result in the two phases being “unlinkable”. While the server is able to tell whether a token presented for redemption was previously generated by interacting with a rightful client, it cannot link the token to a specific token generation phase.
Crucially, tokens are single-use: servers keep track of which tokens have already been redeemed to avoid multiple redemptions. Furthermore, clients should not present the same token twice to prevent different redemption phases from being linked.
Tokens have a fixed life span. If they are too old, they will stop being redeemable. In that case, a new token generation phase must be initiated by the client to obtain new tokens.
Kagi’s implementation of Privacy Pass
Deployment model
As standardized in [2 - 4], the Privacy Pass protocol is able to accommodate many “architectures.” Our deployment model follows the original architecture presented by Davidson et al. [1], called “Shared Origin, Attester, Issuer” in § 4 of [2].
Here, Kagi plays all the “Server roles” (Attester, Issuer, Origin), and Kagi users play the Client role via the new Kagi browser extensions for Privacy Pass, or via native support in Orion. This is what it looks like in practice:
- Once installed, and periodically, the browser extension will generate and store a large number of tokens.
- The user can mark in the extension whether searches should be performed by authenticating classically via a session cookie, or by using Privacy Pass.
- If the user chooses the second option, they will authenticate to Kagi during the search by redeeming one of the tokens it previously generated.
Technical details
Full technical details of the implementation are available in our documentation.
Usage
Using Privacy Pass is as easy as clicking a toggle.
Orion browser
If you are using the latest version of Orion for macOS, select Kagi as your search engine in Settings -> Search and then enable the checkbox for showing Privacy Pass options on your toolbar.
From there you can easily toggle when you want to use Privacy Pass or standard authentication.
On iOS and iPadOS, Kagi Privacy Pass is natively supported in the latest version of the Orion Browser for iOS and iPadOS and takes just a few clicks to enable.

Kagi app for Android
Our Android app now supports Privacy Pass mode via an app shortcut. Launching the shortcut allows you to browse Kagi seamlessly in Privacy Pass mode. You can also add the shortcut to your home screen for quick access.
This feature lets you either use Kagi exclusively in Privacy Pass mode or switch effortlessly between modes.
Chrome and Firefox browser extensions
If you are using the Kagi Privacy Pass extension for Chrome or Firefox, once installed you should see the Kagi Privacy Pass icon on your toolbar.
Once installed, the extension automatically generates tokens. To use them, click the extension icon, and make sure the toggle is on.
Note that Safari is not supported at this moment; see the F.A.Q. below for more information.
What guarantees does Privacy Pass offer?
As used by Kagi, Privacy Pass tokens offer various security properties (§ 3.3, of [2]).
These can be a little technical to capture. In a few words, they guarantee that users can trust that their searches authenticated via Privacy Pass cannot be linked to their accounts, and Kagi can rest assured that only legitimate users can correctly authenticate using Privacy Pass. Crucially, the guarantee for users is even against malicious servers that attempt to incorrectly implement the server-side computation, as long as the client-side implementation is correct.
Three of these security properties serve to protect our users:
Generation-redemption unlinkability: Kagi cannot link the tokens presented during token redemption (i.e. during search) with any specific token generation phase. This means that Kagi will not be able to tell who it is serving search results to, only that it is someone who presented a valid Privacy Pass token.
Redemption-redemption unlinkability: Kagi cannot link the tokens presented during two different token redemptions. This means that Kagi will not be able to tell from tokens alone whether two searches are being performed by the same user.
No redemption hijacking: an eavesdropper that observes any token generation phase, cannot use the observed information alone to “steal” the tokens from the intended user and redeem them themselves. This means that third parties snooping on a user’s token generation interaction will not be able to steal the tokens. This adds a layer of security on top of the confidentiality attained during token generation by using a TLS-protected connection.
Two of these security properties serve to protect Kagi.
Correctness: honestly generated tokens will pass Kagi’s validation.
One-more-forgery security: a malicious client cannot use knowledge of a correctly generated token to forge a new one. This means that valid tokens cannot be generated without correctly interacting with Kagi, and therefore valid tokens are evidence that the user owned a valid session cookie for a supported Kagi plan at the moment of generating the token.
Is Privacy Pass a silver bullet for all your privacy needs?
Naturally, online interactions are never fully described by a mathematical model.
While the Privacy Pass protocol does indeed guarantee that the server will not be able to link token generation and token redemption phases from the tokens alone, in principle, a malicious server could still attempt to track clients via side-channel information.
For example, if someone were to make the same specific request to a server at the same time every day (say, searching “lunch places near 123 Mulholland Drive, LA” at 11:58 AM), a server that records all searches being made could, in principle, guess that these searches are all made by the same person.
In this case, Privacy Pass would make it harder for the server to determine who this specific person is, but the server could nonetheless link searches to one another.
On a level beyond, it is well known that browsers can often have a unique “fingerprint” [5-7]. Fingerprinting attacks heavily rely on side-channel signals that evade the Privacy Pass protocol, such as user-agent strings or IP addresses. For example, if a server receives a token generation request from a given IP address, and immediately after a token redemption request from the same address, it can likely conclude that the same individual is behind the request. For this reason, it is highly recommended to separate token generation and redemption in time, or “in space” (by using an anonymizing service such as Tor when redeeming tokens, see below).
Kagi’s Privacy Pass extension and native implementation in Orion take care, as much as we can, to uniform your browser fingerprint, by removing deanonymizing HTTP headers and cookies.
We see Privacy Pass as an important tool for increasing the anonymity guarantees we can offer to Kagi users.
Adopting state-of-the-art standards for new privacy enhancing technologies also signals to researchers and standardization bodies that there is a public demand for more privacy and anonymity tools in today’s digital world and incentivizes further scrutiny and development of privacy-enhancing technologies.
Kagi Tor service

Together with launching Privacy Pass, we are also announcing that we now have a Tor onion service available, which allows access to Kagi directly from the Tor network. Kagi’s onion address is:
kagi2pv5bdcxxqla5itjzje2cgdccuwept5ub6patvmvn3qgmgjd6vid.onion
On its own, Tor will obscure your location by hiding your IP address. However, without Privacy Pass, you still need to be logged into your Kagi account to perform searches, making them all theoretically linkable back to a single account. As always, Kagi does not link searches to accounts or permanently record them; see our Privacy Policy for more info.
With Tor and Privacy Pass together, Kagi only knows that the search is being issued by a user who previously verified that they have an account authorized to receive tokens, but nothing about the user’s account, or where they’re located.
See more information about Kagi Tor service in our documentation.
Start using Kagi Privacy Pass
Privacy Pass support is provided:
- Natively for Orion browser users (macOS/iOS/iPadOS)
- Natively through Kagi App for Android
- Browser extension for Firefox or Chrome
This should accommodate users who want to install and use the extension across multiple browsers or computers. Please refer to our documentation for usage instructions.
At first, Privacy Pass authentication will be available to users on any Kagi plan with unlimited searches. These plans will have a generous allocation of tokens (2000 to begin with) that they can generate monthly.
We are working on enabling this feature for Trial and Starter plans, which have access to a limited number of monthly searches. Therefore, they risk a worse user experience if their generated tokens are lost (for example, due to uninstalling the extension) and theoretically, users on this plan could redeem more tokens than the limit of searches allowed on their plan (again, we do not know who the user redeeming the tokens is, or what plan they are on). This makes it more technically challenging to support these plans with Privacy Pass, and we have left that for later.
Frequently asked questions
You mention “tokens.” Are blockchains involved in this protocol?
Privacy Pass does not rely on any blockchain technology.
While the protocol makes use of various cryptographic primitives (specifically, elliptic curves and hash functions, as part of a “verifiable oblivious pseudorandom function” construction, [8]) and generates “tokens,” these are not generated, stored, or traded on a blockchain.
You mention the client generating tokens. Is this process energy-intensive or storage-demanding?
No. The generation of 500 search tokens requires approximately 1 second of computation on a consumer laptop, and is performed in the background when installing the extension. A few extra seconds may be required due to the time required to contact the server and get a response. Each token consists of 216 bytes, for a total of approximately 100 KiB of storage per token generation request.
Is there a potential impact on the speed of search when using Privacy Pass?
The initial generation of tokens takes about ~1 second for 500 tokens, plus the time required for contacting the server. This occurs infrequently and is done in the background when possible.
Currently, the token validation servers are only deployed in our us-central1 region, we plan to expand this shortly after launch.
How many tokens am I able to generate?
You can generate 2,000 tokens in one “epoch” (= one month). This should be enough for most users. If you need more than this, you can request additional tokens by contacting support@kagi.com.
Do you plan to allow purchasing privacy pass tokens without having an account?
Yes, this makes sense. This is possible because technically the extension does not care if you have an account or not. It just needs to be ‘loaded’ with valid tokens. And you can imagine a mechanism where you could also anonymously purchase them, eg. with monero, without ever creating an account at Kagi. Let us know here if you are excited about this, as it will help prioritize it.
How can I submit feedback for Kagi Privacy Pass?
We have a feedback thread open here.
Even if the extension implements anti-fingerprinting measures, Kagi will still be able to see my IP address, correct?
Even with Privacy Pass authentication enabled, due to the way the TCP/IP stack works, we will be able to see your search request come from an IP address. As outlined in our Privacy Policy, your privacy is our priority, whether you are using Privacy Pass to authenticate or otherwise. If you are worried about us seeing your IP address, our suggestion is to connect to Kagi via Tor or through a VPN service you trust.
How can Privacy Pass increase my privacy, if I have to send a session cookie to authenticate during token generation?
While token generation is indeed not anonymous, Privacy Pass provides you with anonymity during search.
By providing the server with a Privacy Pass token instead of a session cookie when searching, you will guarantee that your searches cannot be linked to any specific user account that generated Privacy Pass tokens, or to each other.
From the point of view of the server, your search query could have come from any of the users who previously generated Privacy Pass tokens.
The more users do so, the lower the probability that the server can guess it was you specifically who made a given search query.
Token generation does not work in my Chrome/Firefox private window
Correct, we need to authenticate you to create tokens (see above), and in the private window, the extension does not have access to your session cookie. Please use a normal browsing window while logged in to Kagi to generate tokens.
Note, generating tokens while in a private window will work in the Orion browser.
Can I use Kagi Assistant while using Privacy Pass?
Not at this time, since Kagi Assistant is only available to Ultimate members. In Privacy Pass, we don’t have any account information, so we can’t validate what plan you’re on. We could issue tokens attached to different keys for different plans, but that also has privacy implications, see the discussion of personalization below.
What Kagi services will be compatible with Privacy Pass at launch?
At launch, Privacy Pass will only be used to authenticate Kagi Search. Soon to follow (in the next few weeks), we plan to expand support for Kagi Privacy Pass to:
- Kagi Assistant
- Kagi Translate and Kagi Maps
- Kagi universal Summarizer and Ask questions about page
Please disable Privacy pass to access these services for now.
Since initial token generation happens in batches and the tokens expire, could tokens with similar expiration dates potentially be used to identify multiple searches from the same user?
All tokens generated during month X expire at midnight of the first day of month X+2, to avoid this exact issue. Meaning a freshly generated token lasts until the end of the month following its generation (generate today, use all of Feb and March).
If Kagi cannot track who exactly is performing search queries, will I have access to my account settings including customization and personalization?
Since Kagi will not know who you are, we will not be able to serve you content tailored to your custom settings via Privacy Pass-protected search.
We have considered allowing users to send a small configuration with every request (language, region, safe-search) to automatically customize your search experience to some extent. However, we currently believe this would quickly result in a significant loss of anonymity for you and for other users. To illustrate this, we have examined the most common configurations of (language, region, search-safe) used on Kagi.com, and extrapolated how many Privacy Pass users would share them. Looking at the top 35 configurations, we see the following approximate numbers.
| # PP users: | 100 | 1000 | 10 000 | 100 000 | 1 000 000 | 10 000 000 |
|---|---|---|---|---|---|---|
| Config 1 | ≈ 20 | ≈ 200 | ≈ 2000 | ≈ 20000 | ≈ 250000 | ≈ 2490000 |
| Config 2 | < 10 | ≈ 80 | ≈ 800 | ≈ 8000 | ≈ 80000 | ≈ 810000 |
| Config 3 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 | ≈ 450000 |
| Config 4 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 | ≈ 430000 |
| Config 5 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 | ≈ 390000 |
| Config 6 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 | ≈ 370000 |
| Config 7 | < 5 | ≈ 30 | ≈ 300 | ≈ 3000 | ≈ 30000 | ≈ 340000 |
| Config 8 | < 5 | ≈ 30 | ≈ 300 | ≈ 3000 | ≈ 30000 | ≈ 290000 |
| Config 9 | < 5 | ≈ 30 | ≈ 300 | ≈ 3000 | ≈ 30000 | ≈ 260000 |
| Config 10 | < 5 | ≈ 20 | ≈ 200 | ≈ 2000 | ≈ 20000 | ≈ 230000 |
| … | ||||||
| Config 574+ | 0 | 0 | 0 | 0 | < 5 | ≈ 30 |
Limiting the analysis to only the ten most common language settings, the effect is similar:
| # PP Users: | 100 | 1 000 | 10 000 | 100 000 | 1 000 000 | 10 000 000 |
|---|---|---|---|---|---|---|
| Lang 1 | ≈ 100 | ≈ 1000 | ≈ 10000 | ≈ 100000 | ≈ 970000 | ≈ 9660000 |
| Lang 2 | 1 | < 10 | ≈ 90 | ≈ 900 | ≈ 9000 | ≈ 90000 |
| Lang 3 | 1 | < 10 | ≈ 70 | ≈ 700 | ≈ 7000 | ≈ 70000 |
| Lang 4 | 0 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 |
| Lang 5 | 0 | < 5 | ≈ 40 | ≈ 400 | ≈ 4000 | ≈ 40000 |
| Lang 6 | 0 | < 5 | ≈ 30 | ≈ 300 | ≈ 3000 | ≈ 30000 |
| Lang 7 | 0 | < 5 | ≈ 20 | ≈ 200 | ≈ 2000 | ≈ 20000 |
| Lang 8 | 0 | 1 | ≈ 10 | ≈ 100 | ≈ 1000 | ≈ 10000 |
| Lang 9 | 0 | 1 | ≈ 10 | ≈ 100 | ≈ 1000 | ≈ 10000 |
| Lang 10 | 0 | 1 | ≈ 10 | ≈ 100 | ≈ 1000 | ≈ 10000 |
This would mean that someone sending us Lang 10 as their language configuration would automatically lose redemption-redemption unlinkability guarantees if approximately 1000 Kagi users used Privacy Pass.
While our extrapolation may be overly conservative, we won’t be enabling this level of “default” customization for users authenticating via Privacy Pass for the time being. We could reconsider if we find a better solution.
For manual search settings customization, you can always use bangs in your search query to enable basic settings for a specific query. For example, regional bangs will let you focus your query on one region. For example prefixing your search with !de will automatically search in the German region.
To access a fully customized search experience, you can always use the traditional login method and disable the use of Privacy Pass.
Will Safari be supported?
The Safari extensions API doesn’t support (as far as we know) removing cookies from requests, which means it will always authenticate with your logged-in account. We’re not aware of a way to change this. The alternative if you want a similar, native, WebKit-based browsing experience, is to use the Orion Browser which has Kagi Privacy Pass natively integrated.
References
- Davidson, A., Goldberg, I., Sullivan, N., Tankersley, G., & Valsorda, F. (2018). Privacy pass: Bypassing internet challenges anonymously. Proceedings on Privacy Enhancing Technologies. Paper.
- Davidson, A., Iyengar, J., & A. Wood, C. (2024). The Privacy Pass Architecture. RFC 9576.
- Pauly, T., Valdez, S., & A. Wood, C. (2024). The Privacy Pass HTTP Authentication Scheme. RFC 9577.
- Celi, S., Davidson, A., Valdez, S., & Wood, C. A. (2024). Privacy Pass Issuance Protocols. RFC 9578.
- Eckersley, P. (2010). How unique is your web browser? Proceedings on Privacy Enhancing Technologies. Paper.
- EFF. Cover your tracks. https://firstpartysimulator.org/learn
- EFF (2010). Panopticlick. https://pbtest.org/about#browser-fingerprinting
- Davidson, A., Faz-Hernandez, A., Sullivan, N., & A. Wood, C. (2023). Oblivious Pseudorandom Functions (OPRFs) Using Prime-Order Groups. RFC 9497.
Do you like how this post reads? It was proofread with Kagi Translate’s proofreading option. To proofread any web page, just use
https://translate.kagi.com/proofread/[URL].